A Comprehensive Guide to Securing Your Wi-Fi Network – An Essential Step in Building Your Cryptocurrency Fortress.


Most routers, when first taken out of the box with their default settings, leave your internet connection vulnerable to cyber threats. Surprisingly, the vast majority of users simply plug them in and don’t bother with adjusting the settings to utilize all the security features. In this comprehensive guide, we will walk you through the essential steps to secure your home or office Wi-Fi network. Follow this step-by-step guide to create a safe and secure environment for all your financial and cryptocurrency operations.
Review And Change The Following Wi-Fi Router Settings:
Step 1: Change Your SSID (Wi-Fi Network Name)
The settings panel will vary from router to router, but the option you are looking for should be under the ‘Wireless’ tab.
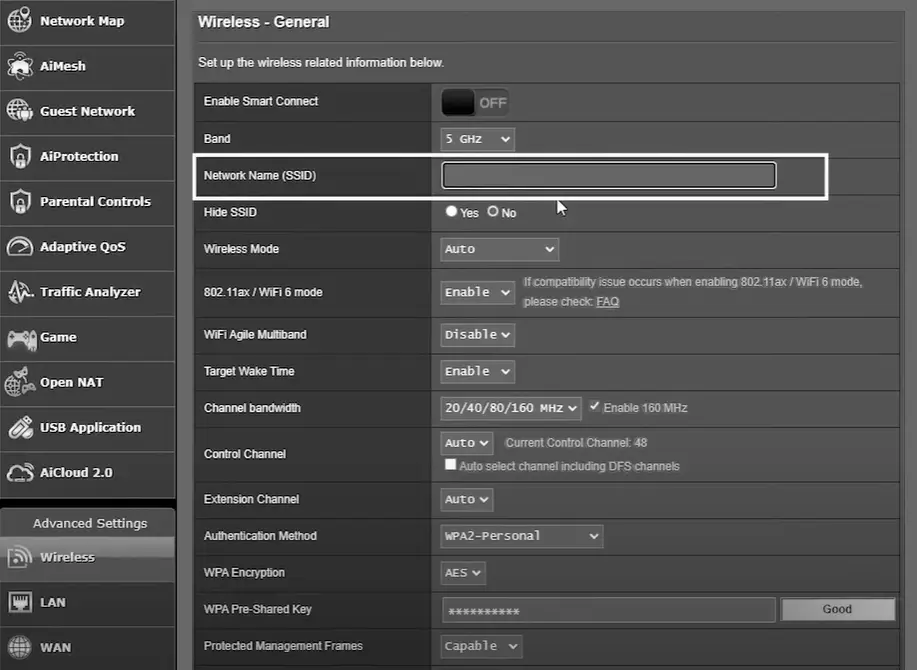
- Log in to your router’s administration panel. You can usually access this by entering the router’s IP address in a web browser.
- The default IP address for most routers is: 192.168.1.1, or 192.168.0.1 – admin: ‘admin’, and for the password: ‘admin’.
- Locate the SSID (network name) settings.
- Change your SSID to something unique and not personally identifiable. Avoid using default SSIDs that may be associated with your router’s manufacturer.
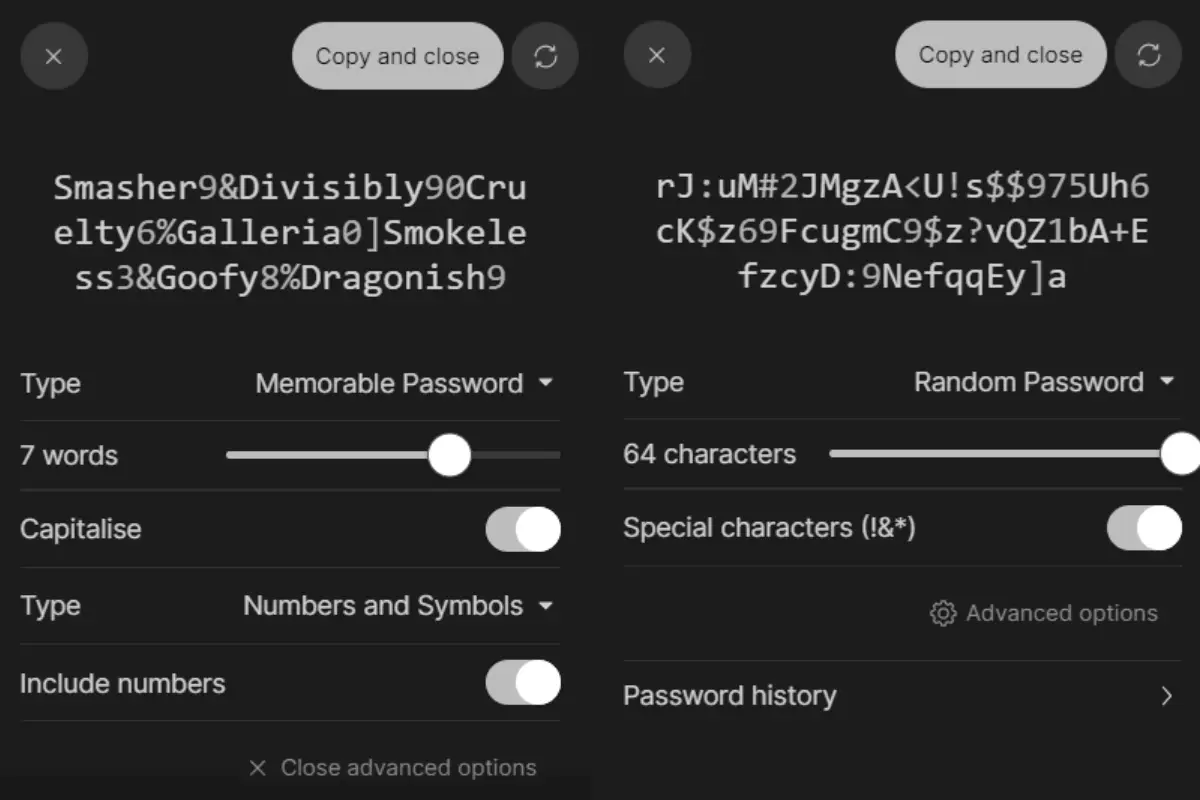
Step 2: Create a Strong, Unique Password
- Generate a strong, unique Wi-Fi password. Use a password manager or generator to ensure its strength.
- A strong password typically includes a combination of upper and lower-case letters, numbers, and special characters.
- Avoid using easily guessable passwords, such as “123456” or “password.”
Step 3: Disable Remote Access
- In your router’s settings, disable remote access to your router. This prevents unauthorized users from remotely accessing your network.
- Remote access is generally an advanced feature and not necessary for most users.
Step 4: Set Up a Guest Network
- Create a separate Wi-Fi network for guests and Internet of Things (IoT) devices to prevent them from accessing your primary network.
- This can be done by using a router with a guest network feature or setting up a separate router.
Step 5: Turn Off Wi-Fi When Away
- When leaving your home for an extended period, turn off your Wi-Fi network to prevent unauthorized access during your absence.
- This reduces the risk of potential hackers gaining access to your network while you’re not at home.
CRYPTO TOOLBOX
Additional Steps For Increasing Router Security:
Step 6: Regular Firmware Updates
- Regularly check for firmware updates for your router and apply them promptly. Updates often include security patches to protect against vulnerabilities.
Step 7: Enable WPA3 Encryption
- Ensure your Wi-Fi network is using WPA3 encryption, which is more secure than older encryption protocols.
- This can be found in your router’s security settings.
Step 8: MAC Address Filtering
- Consider enabling MAC address filtering. This feature allows you to specify which devices are allowed to connect to your network by filtering MAC addresses.
Step 9: Disable WPS
- If your router has Wi-Fi Protected Setup (WPS), disable it. WPS can be vulnerable to brute-force attacks.
Step 10: Guest Network Isolation
- If you have a guest network, enable guest network isolation. This prevents devices on the guest network from communicating with each other.
Tip: When it comes to cybersecurity, it is always a “battle” between security and convinience. Don’t weaken your security and whenever possible chose a cable LAN connection above any Wi-Fi for cryptocurrency-related activities.
Did You Know That You Can Learn A Safe Way To Generate Passive Yield With Your Crypto Over The Next Decade?
Unlock the power of digital assets with HEX Passive Income. This course takes you from novice to pro in the world of cryptocurrency investments in just a few weeks. Learn the secrets of yield farming, PulseChain staking, and the HEX staking ladder system. Get started today for financial freedom.
Most Popular Treats And Exploits Of Wi-Fi Networks
Let’s discuss some of the most popular threats and methods hackers use to exploit Wi-Fi networks:
1. Unauthorized Access:
- Brute Force Attacks: Hackers attempt to guess your Wi-Fi password by trying various combinations until they find the correct one.
- Default Password Exploitation: Some routers come with default usernames and passwords. If these are not changed, hackers can easily gain access.
2. Eavesdropping:
- Packet Sniffing: Hackers intercept and analyze data packets traveling over the network to capture sensitive information, such as login credentials.
- Man-in-the-Middle (MitM) Attacks: Hackers position themselves between your device and the router to intercept and alter data transmissions.
3. Router Vulnerabilities:
- Firmware Exploitation: Outdated router firmware may have known security vulnerabilities that hackers can exploit. Regular firmware updates are crucial!
- Remote Exploits: If remote access is enabled, hackers may attempt to exploit vulnerabilities in the router’s firmware from anywhere on the internet.
4. Wi-Fi Deauthentication:
- Hackers can flood your Wi-Fi network with deauthentication packets, causing devices to disconnect from the network. This can lead to denial of service (DoS) attacks.
5. Rogue Wi-Fi Networks:
- Hackers may create rogue Wi-Fi networks with similar SSIDs to trick users into connecting to them, allowing for interception of data.
6. Password Cracking:
- Hackers use powerful tools to crack Wi-Fi passwords, especially if they are weak or use easily guessable combinations.
7. Social Engineering:
- Hackers might use phishing techniques to trick users into revealing their Wi-Fi passwords or sensitive information.
8. WPS Vulnerabilities:
- If Wi-Fi Protected Setup (WPS) is enabled on your router, it can be susceptible to brute force attacks, allowing hackers to quickly crack the PIN.
9. DNS Spoofing:
- Hackers may redirect your network’s DNS requests to malicious servers, leading to phishing attacks and website spoofing.
10. Guest Network Exploitation:
- If your guest network is not properly isolated, attackers who gain access can potentially move laterally to your main network.
11. IoT Device Vulnerabilities:
- Internet of Things (IoT) devices often have weak security. Hackers may compromise these devices to gain access to your network.
12. Evil Twin Attacks:
- Attackers create a malicious Wi-Fi network with a name similar to a legitimate network, leading users to connect to the wrong network.
The list above includes only the most common types, but it reveals how dangerous it could be to leave your network unsecured. Now, imagine how risky it would be to visit a café or connect to a public Wi-Fi network and engage in crypto or financial-related operations. In such situations, you not only have ZERO control over the router settings but also have no idea who might be monitoring the traffic behind a public router.
Did You Hear About Our Free E-Book?
There’s much more to becoming successful in crypto, but safeguarding your digital assets is a substantial part. Best of all, it doesn’t have to be complicated. Sign up for our powerful newsletter to enhance your crypto skills right now!
Conclusion
By following these steps and additional security measures, you can significantly enhance the security of your home or office Wi-Fi network. Protecting your network is crucial in today’s digital age, where online privacy and data security are paramount. Make these adjustments to your Wi-Fi network to ensure that your home is a secure place for all your online activities. Securing your internet connection not only safeguards your personal data but also plays a crucial role in improving the security of your cryptocurrency operations. To protect your Wi-Fi network, it’s essential to adhere to the security measures outlined in this guide and remain vigilant against common threats. Regularly updating your router’s firmware, employing strong passwords, and exercising caution with guest network access can substantially reduce the risk of a successful Wi-Fi hack.
Recommended Tools for This Article
PRIVACYPROTON APPS | State-Of-The-Art Privacy Management Suite (incl. Webmail, Password Manager, Drive, VPN, and Calendar)
Proton is a Swiss-Based company that delivers the industry top-level tools to ensure your information is always yours and no one else can read it. As their slogan says “Privacy By Default” – there is much more to it. Sign-up for a free account and check by yourself.
SECURITYDEEPER CONNECT | Decentralized VPN With a 7-Layer Firewall & Enterprise-Grade Security, Offers Unparalleled Protection. No Monthly Fees.
Decentralized Private Network (DPN) is a technology that offers enhanced privacy and security for your internet connection. Unlike traditional centralized VPNs, DPN operates in a peer-to-peer manner, which makes it more secure and private. With DPN, you connect to other nodes or devices instead of a centralized server. This decentralization also makes DPN resistant to censorship, ensuring access to information even in regions with strict online restrictions.









 Don't Let Scammers Win! Discover The Ultimate Defence Strategies For Your Digital Wealth & Secure Your Crypto Future - Now!
Don't Let Scammers Win! Discover The Ultimate Defence Strategies For Your Digital Wealth & Secure Your Crypto Future - Now!