So, you truly desire to ensure that your cryptocurrency remains under your control until you choose to cash it out, free from any ‘interruptions’ or the possibility of someone else making decisions on your behalf to claim it?
If so, the ‘Crypto-Only Laptop’ might be your chance. This article delves into the cutting-edge realm of crypto-exclusive laptops and their undeniable role in fortifying your digital fortress, from warding off keyloggers and malware to enhancing your privacy and mobility. Read on to understand how crypto-only laptops can be your ultimate safeguard in the digital frontier, and why it’s essential to choose wisely in your quest for crypto security. Your crypto journey begins here.
Why Opt for a Crypto-only Laptop?
Privacy Shield:
Crypto-only laptops assist in preserving your privacy by reducing exposure to your personal data and online activities. By dedicating a separate device solely for cryptocurrency-related tasks, you mitigate the risk of cross-contamination with other applications or services that might compromise your privacy.
Confidence and Peace of Mind:
Utilizing a dedicated crypto-only laptop brings peace of mind, assuring you’ve taken significant steps to secure your cryptocurrency holdings and transactions. It provides a dedicated environment that reduces the chances of security breaches, bolstering your confidence in managing and safeguarding your digital assets.
Safeguarding Against Keyloggers and Malware:
Dedicated crypto-only laptops offer robust protection against keyloggers and various forms of malware that pose a threat to your private keys and passwords. By confining the laptop’s use to cryptocurrency-related activities and deploying strong security measures, you substantially reduce the risk of malicious keyloggers capturing keystrokes or malware infiltrating your system.
Trustworthy Hardware and Secure Supply Chain:
Laptops designed only for crypto tasks by reputable manufacturers prioritize the integrity of their hardware and meticulously vet their supply chains. These laptops employ trusted components, minimizing the possibility of compromised or backdoored parts. By choosing a respected brand that emphasizes supply chain security, you can be more confident in the authenticity and integrity of your laptop’s components.
Minimized the Attack Surface:
Crypto-Only laptops typically maintain a lean software stack, with only essential applications and services installed. This streamlined approach trims the attack surface and potential vulnerabilities that malicious actors could exploit. Reducing the software footprint minimizes the likelihood of security breaches.
On-the-Go Privacy and Portability:
Crypto-only laptops provide the flexibility to remain mobile while upholding privacy and security. With a dedicated device, you can conveniently conduct crypto-related activities wherever you go, without relying on potentially untrusted public devices. This portability allows you to access your cryptocurrency wallets, perform transactions, or engage in other crypto tasks discreetly and away from prying eyes.
Offline Security through Airgapping:
Crypto-only laptops can be air-gapped, meaning they’re physically isolated from the internet or potentially compromised networks during sensitive cryptocurrency transactions or wallet management. This adds an extra layer of protection against remote attacks and malware. Airgapping curtails the risk of unauthorized data transfer, enhancing transaction security.
Important: While using a crypto-only laptop bolsters security and privacy for cryptocurrency-related activities, it’s vital to acknowledge the security risks when using the device on the move. When taking your crypto-only laptop outside of controlled environments, like your home or office, you open up the possibility of physical attacks or theft. It’s imperative to stay vigilant and adopt necessary precautions to mitigate these risks.
CRYPTO TOOLBOX
Two Categories of Crypto-Only Laptops
1. Airgapped Crypto-Only Laptops To Serve As A Phisical Vault
Air-gapping, essentially, is like creating a secure fortress for your digital assets. It involves physically isolating your device from the internet and potentially compromised networks by disabling network interfaces such as Wi-Fi and Bluetooth.
The crypto-only laptop can be transformed into an air-gapped device, serving as a secure vault to store and safeguard your cryptocurrency holdings. This strategy significantly reduces the risks associated with remote cyber threats, malware infiltration, and unauthorized data exfiltration. Air-gapping adds an extra layer of protection, ensuring that sensitive cryptocurrency operations, such as storage and offline transaction preparation, occur within a secure and isolated environment.
It’s important to note that for active cryptocurrency trading, exchanges, and online transactions, users may require another ‘Crypto-Only’ laptop that is not air-gapped or temporarily connect the air-gapped laptop to the internet via a cable LAN connection when needed, although doing so may compromise its ‘Internet-isolated’ status.
2. Dedicated Crypto-Only Laptops For Cryptocurrency Operations
This type of crypto-only laptop fulfills the role of a device singularly designated for cryptocurrency-related tasks. By dedicating a distinct device to this specific purpose, you effectively mitigate the risks associated with mixing cryptocurrency activities with other applications or services that may compromise security and privacy.
These laptops serve as unwavering assistants, wholly focused on cryptocurrency-related activities and reinforcing their security through stringent measures. By limiting the device’s utility to cryptocurrency-related functions, you substantially minimize the risk of unauthorized intrusion or interference.
The significance of confining your dedicated crypto-only laptop solely to cryptocurrency tasks cannot be overstated. These specialized devices provide a secure enclave for your digital assets, shielding them from potential threats that may arise when combining crypto operations with email logins, web browsing, or other services.
By maintaining a steadfast focus on cryptocurrency activities and prohibiting unrelated operations, you establish a robust defense against unauthorized intrusion and interference, safeguarding your assets with unwavering dedication. This strict constraint minimizes the risk of compromising your security and privacy, ensuring that your cryptocurrency transactions and holdings remain protected in an increasingly perilous digital landscape.
The Key Considerations for Selecting a Crypto-Only Laptop
Stay Away From Chinese Manufacturers!
When it comes to products originating from China, particularly in the realm of cryptography, there’s a prevalent concern regarding potential backdoors or deliberate vulnerabilities inserted into these products, either by the Chinese government or other entities. This apprehension stems from the perception that the Chinese government wields significant influence over technology companies operating within its borders, potentially exploiting this power to compromise product security.
Backdoors, which are concealed vulnerabilities or deliberate weaknesses in software or hardware, can be exploited to gain unauthorized access or manipulate the system. When products with backdoors are utilized for cryptographic purposes, they can jeopardize the confidentiality, integrity, and authenticity of sensitive information and communications.
This concern arises from the fact that China has enacted laws mandating that companies operating within its jurisdiction cooperate with national intelligence agencies and provide assistance with surveillance or information gathering upon request. This has led to fears that Chinese technology companies might be compelled to incorporate backdoors or weakened encryption in their products.
The apprehension about compromised cryptography in products originating from China is not confined to any particular country or industry. It has garnered global attention and scrutiny, particularly in sensitive sectors such as government, defense, and critical infrastructure, where secure communications and data protection are of paramount importance.
To address these concerns, organizations and governments often subject products to rigorous evaluations, certifications, and security assessments before adopting them for cryptographic purposes. They may also implement additional security measures, like independent audits or alternative cryptography solutions, to mitigate potential risks associated with products sourced from China or any other country.
Pertinent Chinese Legislation:
National Intelligence Law of the People’s Republic of China (2017): This statute authorizes Chinese intelligence agencies to compel organizations and individuals to provide cooperation in aid of intelligence-related efforts, raising apprehensions regarding its potential implications for the security of technology products.
Cryptography Law of the People’s Republic of China (2020): This legislation is designed to oversee the utilization and advancement of cryptography within China, establishing a structured framework for cryptographic algorithms, products, and services. Although it does not explicitly discuss backdoors, questions have arisen concerning possible ramifications for cryptography and the potential for Chinese authorities to access encrypted data.
The Biggest Chinese 'Trojan' To Paralyze Western Cities
Another matter you might have heard of is the information that all Chinese electric cars (EVs), which are enthusiastically owned all around the world, can be remotely controlled or turned off by the Chinese government (if they wanted to disrupt the world’s order).
In a recent article [], concerns raised by Professor Jim Saker, President of the Institute of the Motor Industry in the UK, and former British Conservative Party leader Sir Iain Duncan Smith regarding the security of Chinese-made electric cars, have stirred controversy.
“Anything to do with China is a security threat,” he told The Daily Mail [].
These concerns suggest that these vehicles could be remotely controlled using Trojan horse software, potentially allowing car manufacturers in China to disable a significant number of vehicles across Europe. The debate highlights the cybersecurity implications associated with Chinese products.
Do you think, it would be any harder for such an “equipped” attacker to steal your crypto?
Crypto-Only Laptop Guide: How to Find Laptops Not Made in China?
Not long ago, the majority of electronics were manufactured in Chinese plants due to economic factors. Until the pandemic and the global microchip shortage, not many people paid much attention to it, but it came at an expensive price. Since then, more and more companies have realized that this is no longer an option, and moving away from the Chinese supply chain is a necessity.
However, sourcing all production lines outside of the CCP is not always as easy as it seems. Therefore, it can be challenging to find a laptop that doesn’t contain any parts made there. For this reason, a bare minimum for someone looking for a decent crypto-only laptop would be to ensure that the main, programmable components are not made in China.
Because things are changing rapidly in this matter, instead of creating a list of preferred computers that will soon be outdated, we encourage you to do your research (DYOR).
Therefore, before deciding on a laptop to use exclusively for cryptocurrency, you need to do your homework and find updated information about where the laptop was assembled, as well as the origin of all its components.
Recommended Sources
As a starting point, you may want to read the article on laptops that are not made in China:
Did You Know That You Can Learn A Safe Way To Generate Passive Yield With Your Crypto Over The Next Decade?
Unlock the power of digital assets with HEX Passive Income. This course takes you from novice to pro in the world of cryptocurrency investments in just a few weeks. Learn the secrets of yield farming, PulseChain staking, and the HEX staking ladder system. Get started today for financial freedom.
The Guide to Tech Specifications for a Crypto-Only Laptop
Technical Requrements
Cryptocurrency-dedicated computers can serve as secure ‘vaults’ for storing crypto or be used for active trading. They may even be employed for ‘crypto mining,’ although that is a distinct topic with different technical requirements.
Based on this basic division, various technical expectations should be considered. However, for the purpose of a crypto-only laptop used as a digital currency vault or a device solely for buying/selling cryptocurrencies, the good news is that you don’t need any extra computing power.
Any laptop with technical specifications sufficient for web browsing should be adequate.
OS (Operating System)
If you followed this crypto-only laptop guide and your objective is to make your computer air-gapped, the choice of operating system depends solely on your preferences.
However, it’s worth noting that iOS is considered less vulnerable to exploits than Windows, followed by Linux, which is widely recognized as the most secure OS.
RAM Memory
Ideally, ensure it has enough RAM because the more it boasts, the smoother your browsing experience will be.
For instance, a laptop with 4GB RAM will start to slow down with 7-8 browser tabs open. So, it’s advisable to opt for a minimum of 16 GB of RAM.
Hard Drive
You should also choose an SSD drive, as it will make your laptop work smoothly and is less vulnerable to damage, as Solid State Drives do not have movable parts. The capacity doesn’t matter here.
GPU
When it comes to Graphic Cards, it’s up to you. These days, most modern laptops come with a basic graphics card because it helps the processor, but you don’t have to go overboard in this area.
CPU
Lastly, the processor requirements for a crypto-only laptop are the same as those advised for regular office tasks.
Crypto-Only Laptop Guide: Best Practices
Physical Security:
Ensure your crypto-exclusive laptop remains within your control, refraining from leaving it unattended in public areas. Employ a secure bag or case equipped with anti-theft features to protect your device from theft or tampering, and always activate screen lock when not in active use.
Internet Connection Security:
Rely on your personal/mobile internet connection and steer clear of public Wi-Fi networks, which may lack the necessary security, potentially exposing your cryptocurrency-related activities.
Screen Privacy:
Whenever feasible, operate your crypto laptop in private surroundings. Alternatively, employ a privacy filter or adjust the screen’s viewing angle to prevent unauthorized access to your sensitive cryptocurrency information.
Data Encryption:
Ideally, activate encryption mechanisms such as Bitlocker on all drives to thwart data access in case of theft or loss.
Secure Storage:
Safely store your laptop when not in use, whether in a locked compartment or a secure safe, to prevent unauthorized access and reduce the susceptibility to physical attacks targeting your device and valuable cryptocurrency assets.
Privacy Tools:
Always, utilize:
for enhanced security during your crypto operations.
Password Protection:
Implement a strong screen lock password to fortify access control. The same applies to the user account. Utilize a reputable, end-to-end encrypted password manager.
Limited User Account:
Create a dedicated user account devoid of administrative privileges and exclusively employ it for cryptocurrency operations.
Antivirus Protection:
Use reputable antivirus software.
Always Use Hardware Wallet:
Regardless of the crypto-only laptop security measures, always utilize a hardware wallet. Create a strong and secure backup of your cryptocurrency wallets and ensure you maintain a secure offline copy of your private keys or recovery phrases. This strategy ensures that even in cases of loss, theft, or compromise of your crypto-only laptop, you retain the ability to regain access to your funds, minimizing potential losses.
Bear in mind that while these measures significantly enhance security, no security arrangement is entirely impervious. It is crucial to evaluate the risks specific to your situation and take appropriate precautions to shield your crypto-only laptop and assets from physical threats, particularly when you are on the move.
Did You Hear About Our Free E-Book?
There’s much more to becoming successful in crypto, but safeguarding your digital assets is a substantial part. Best of all, it doesn’t have to be complicated. Sign up for our powerful newsletter to enhance your crypto skills right now!
Crypto Laptop – Questions & Answers
Why should I consider using a crypto-only laptop?
Using a crypto-only laptop offers several benefits, including enhanced privacy, protection against keyloggers and malware, trustworthy hardware, minimized attack surface, mobile privacy, and the option for offline security through airgapping.
What are the two main categories of crypto-only laptops?
There are two categories of crypto-only laptops:
- airgapped crypto-only laptops that act as secure vaults for cryptocurrency storage, and
- dedicated crypto-only laptops designed solely for cryptocurrency operations.
How can I ensure my crypto-only laptop is not made in China?
To ensure your crypto-only laptop is not made in China, research and purchase a laptop from a reputable manufacturer that clearly states its country of origin, such as Taiwan or the United States. Verify the laptop’s components and supply chain, and consider open-source hardware options. Additionally, you can consult tech forums and reviews to gather information about the laptop’s manufacturing origin. Please refer to the chapter in this article for more details.
What are the best practices for secure cryptocurrency operations on a crypto-only laptop?
To ensure secure cryptocurrency operations, follow practices like maintaining physical security, using a personal internet connection, employing screen privacy measures, activating data encryption, utilizing a hardware wallet, and more. Please refer to the chapter in this article for more details.
Why is safeguarding your digital assets with a crypto-only laptop important?
Safeguarding digital assets with a crypto-only laptop is important because it can enhance security by isolating your cryptocurrency-related activities from potentially compromised or insecure devices. This dedicated laptop can be configured with robust security measures, reducing the risk of malware, phishing, or other threats. It also ensures that private keys and sensitive data are less exposed to potential security breaches, offering greater protection for your cryptocurrency investments.
Can a crypto-only laptop ensure I am 100% protected against losing my digital assets?
While crypto-only laptops significantly enhance security and privacy for your digital assets, no security measure is entirely impervious. When using a crypto-only laptop outside controlled environments, you expose it to potential physical attacks or theft. It’s essential to stay vigilant and take necessary precautions to minimize these risks. For enhanced protection always use a hardware wallet in conjunction with the crypto-only laptop.
Can I use my crypto-only computer for other, unrelated tasks?
It’s recommended to use your crypto-only laptop exclusively for cryptocurrency-related activities. Mixing these tasks with unrelated activities can compromise your security and privacy. By maintaining a dedicated focus on cryptocurrency operations, you establish a robust defense against unauthorized intrusion and interference.
What if I want to invest only a small amount of money in cryptocurrencies? Do I still need to buy a dedicated laptop for that?
The level of investment doesn’t necessarily dictate the need for a dedicated laptop. If you’re dealing with a small amount of money, you can still follow security best practices on your regular laptop. However, ensure your regular laptop is adequately secured and up-to-date to protect your digital assets. At a minimum, invest in a hardware wallet (which is usually much cheaper than a new laptop, yet it offers the highest level of security).
What if I can't afford to buy a new laptop right now? Should I restrain from investing in crypto?
If purchasing a new laptop isn’t feasible, you can still invest in cryptocurrencies on your existing device, but take extra precautions. Keep your system and security software updated, use strong passwords, and consider using a hardware wallet for added protection.
Can I use my regular laptop to buy cryptocurrencies?
Yes, you can use your regular laptop to buy cryptocurrencies, but it’s crucial to implement strong security measures. Use a secure and updated system, enable two-factor authentication, and ensure your private keys are stored safely (always use a hardware wallet to protect them). A dedicated crypto-only laptop is recommended for enhanced security.
Is it acceptable to buy a laptop for crypto-related activities from second hand?
Although buying a second-hand laptop for crypto-related activities carries additional risks, it is acceptable only if you can verify its history and ensure it hasn’t been compromised or tampered with. Thoroughly inspect the device, reformat it, and install a fresh operating system to enhance security. For additional protection always use a hardware wallet.
I bought a new laptop to use solely for crypto operations. Can I give away my old laptop I used for crypto?
Giving away your old laptop, which was used for crypto, is acceptable only if you removed and destroyed the hard drive and performed a factory reset. This is because your “old” data can be retrieved with sophisticated software, even if you’ve erased it. If you allowlisted your old laptop to connect to your Wi-Fi or certain online services, bear in mind that this laptop can potentially be used to exploit your security unless you’ve revoked such permissions.
If I had to choose between buying a crypto-only laptop or investing in a hardware wallet to use with my regular laptop, which would be a more secure option?
If you prioritize security for your cryptocurrency investments, a hardware wallet for your regular laptop is often considered a more secure option. Hardware wallets provide an extra layer of protection by storing your private keys offline, making them less vulnerable to online threats. However, a crypto-only laptop can complement this security strategy, especially if you need a dedicated, secure environment for your crypto activities.
Conclusion
Armed with a fundamental understanding of how necessary it is to isolate all your crypto-related activities from regular tasks and possessing solid knowledge on how to choose a device to serve as a crypto-only laptop, you set yourself apart from the failures that await the average crypto holder. You have laid a foundation for building your secure crypto empire, but bear in mind that there is much more to it in order to sustain your cryptocurrency investments. Protecting your life savings or even smaller investments held as cryptocurrency is not optional. It may seem like a tedious job to follow all these rules and requirements, but remember that people who achieve extraordinary results do extraordinary things that others are not willing to do.
Recommended Tools for This Article
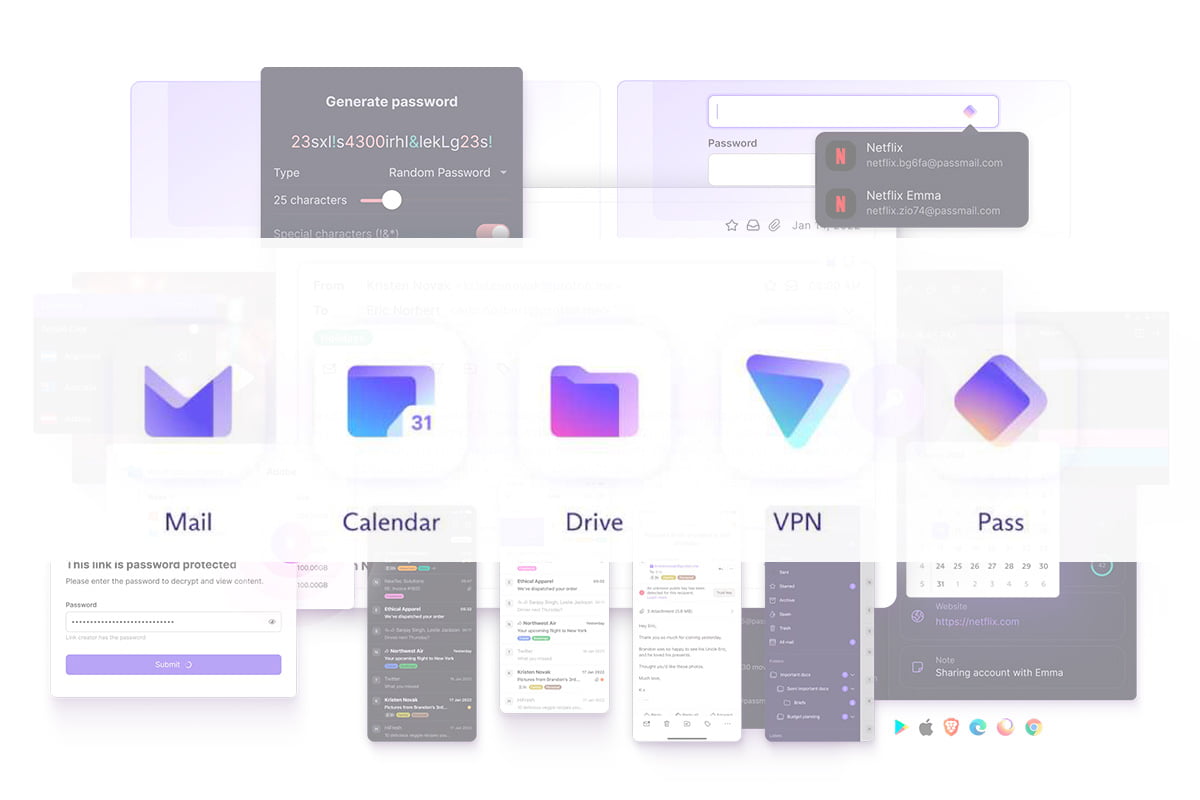
PRIVACYPROTON APPS | State-Of-The-Art Privacy Management Suite (incl. Webmail, Password Manager, Drive, VPN, and Calendar)
Proton is a Swiss-Based company that delivers the industry top-level tools to ensure your information is always yours and no one else can read it. As their slogan says "Privacy By Default" - there is much more to it. Sign-up for a free account and check by yourself.
SECURITYDEEPER CONNECT | Decentralized VPN With a 7-Layer Firewall & Enterprise-Grade Security, Offers Unparalleled Protection. No Monthly Fees.
Decentralized Private Network (DPN) is a technology that offers enhanced privacy and security for your internet connection. Unlike traditional centralized VPNs, DPN operates in a peer-to-peer manner, which makes it more secure and private. With DPN, you connect to other nodes or devices instead of a centralized server. This decentralization also makes DPN resistant to censorship, ensuring access to information even in regions with strict online restrictions.
SECURITYTREZOR | Most Secure And Time-Proven Hardware Wallet
Grab your Trezor device, plug it in, open Trezor Suite, and let your crypto journey begin. Let The Trezor Hardware Wallet Shield Your Digital Assets Now!











 Don't Let Scammers Win! Discover The Ultimate Defence Strategies For Your Digital Wealth & Secure Your Crypto Future - Now!
Don't Let Scammers Win! Discover The Ultimate Defence Strategies For Your Digital Wealth & Secure Your Crypto Future - Now!