In an age where our lives are increasingly intertwined with the digital realm, the importance of safeguarding our online presence cannot be overstated. Cybersecurity threats, particularly phishing attacks, lurk in the virtual shadows, targeting individuals and organizations alike. To shield ourselves effectively, it’s crucial to not only understand the nature of phishing but also to recognize and thwart these deceptive ploys. In this chapter, we’ll embark on a journey to protect against phishing attacks, equipping you with knowledge and tools to defend your digital fortress.
Understanding Phishing Threats
Unveiling the Art of Deception
Phishing attacks come in various forms, all designed to trick you into making a costly mistake. At its core, phishing is a form of cybercrime that relies on deception. Cybercriminals masquerade as trustworthy entities, using emails, messages, or websites that appear legitimate to lure individuals into revealing sensitive information such as login credentials, credit card details, or personal data.
Variants Of Phishing
Phishing comes in various forms, each designed to exploit specific vulnerabilities:
Spear-Phishing
In this targeted approach, cybercriminals customize their attacks, often impersonating a known contact or organization to gain trust. Adversaries tailor these attacks based on personal information they have about you. For instance, you might receive an email from someone you know, containing seemingly innocuous content. However, the attached document may contain malware designed to infiltrate your device. Be vigilant, as attackers can exploit known relationships to deceive you.
Whaling
This variant focuses on high-profile targets like executives or public figures, seeking to compromise their accounts.
Phishing for Passwords (aka Credential Harvesting)
Phishers often employ deceptive links to trick you into revealing your login credentials. These links may appear legitimate at first glance but redirect you to malicious websites. To avoid falling victim, always scrutinize the address bar in your web browser. Verify that it matches the legitimate website’s domain before entering your login information. Phishers may also use lookalike letters or similar domain names to deceive you, so exercise caution.
Vishing
Here, the attack occurs over the phone, with scammers posing as legitimate entities to extract information verbally.
Usually, phishing attacks take the form of a message designed to convince you to:
Click on a provided link…
Open an attached document…
Install software on your device…
Enter your username and password on a website that appears genuine…
Connect your crypto wallet to a website, to receive a free airdrop (free cryptocurrencies)…
and more…
It’s crucial to understand that falling victim to phishing attacks can lead to serious consequences. These deceptive tactics can trick you into disclosing your confidential passwords or unwittingly installing malicious software on your device. This gives attackers the power to remotely control your device, steal sensitive information, or even spy on your online activities.
Cybercriminals employ cunning tactics to lure unsuspecting victims into connecting their digital crypto wallets to malicious websites, ultimately aiming to record the victim’s physical IP address. This sinister ploy becomes especially menacing when the wallet holds a substantial amount of cryptocurrency, as it allows the criminals to pinpoint the owner’s physical location on a map, opening the door to potential physical threats and extortion!
However, most often phishing perpetrators employ deceptive strategies aimed at acquiring your login credentials. They distribute misleading links that, at first glance, seem to direct you to one location but, in reality, lead elsewhere. To verify the actual destination of a link, you can hover your cursor over it. Even though, it’s worth noting that these links can be camouflaged using letters that closely resemble legitimate ones or by employing domain names with subtle alterations. This crafty tactic aims to trick individuals into entering their usernames and passwords on imitation login pages, which often bear a striking resemblance to the authentic ones. It’s crucial to exercise caution and inspect your web browser’s address bar thoroughly before entering any sensitive information.
To illustrate the gravity of phishing attacks, let’s consider a real-life situation:
Real-Life Example: The PayPal Impersonation
Imagine receiving an email seemingly from PayPal, claiming there’s been suspicious activity on your account. It urges you to click a link to verify your information. However, upon closer inspection, you notice that the email address is misspelt, and the URL doesn’t lead to the official PayPal site. This is a classic phishing attempt.
Example:
In some instances, these phishers go a step further by creating websites that closely mimic well-known web addresses, making it challenging to distinguish between the real and the counterfeit.
For instance, https://wwwpaypal.com/ is distinct from https://www.paypal.com/.
Similarly, https://www.paypal.com/ (with a capital “i” instead of a lowercase “L”) differs from https://www.paypal.com/.
Understanding these threats is the first step in protecting yourself against them.
CRYPTO TOOLBOX
Recognizing Phishing Attempts
Generic greetings
Urgent language
Susipicious links
Unexpected Attachments
Unsolicited Messages
Weird messages from friends
Did You Know That You Can Learn A Safe Way To Generate Passive Yield With Your Crypto Over The Next Decade?
Unlock the power of digital assets with HEX Passive Income. This course takes you from novice to pro in the world of cryptocurrency investments in just a few weeks. Learn the secrets of yield farming, PulseChain staking, and the HEX staking ladder system. Get started today for financial freedom.
Defending Against Phishing Attacks
Building Digital Resilience
Verify the sender
Be cautious of emailed instructions
Hover, don't click
Use link "un-shorteners"
If you receive a shortened URL, such as one from Twitter in the form of a t.co link, it’s advisable to use an “unshortener” service, such as: checkshorturl.com to unveil its true destination.
Open suspicious documents in a cloud service
Attachments from unknown sources can be risky. Instead of directly opening downloaded files, upload them to Google Drive or a similar online document reader. This precaution converts the document into a safer format, reducing the risk of malware infection.
Be advised, however, that the employees of services, such as Google, have full access to your files stored in their clouds, so they can read your files and documents (refer to Google’s TOS).
Use a Password Manager with auto-fill
Enable 'Two-Factor Authentication' (2FA)
Hide your IP address with a VPN
Install a reputable Anti-Virus
Modern Anti-Viruses act also pro-actively warns you and helps to prevent opening fraudulent links or clicking suspicious links.
Keep your software updated
Educate yourself
Report Suspected Phishing
If you receive a phishing email, report it to the legitimate organization it impersonates. This helps them take action against cybercriminals. By adhering to these safe practices, you can significantly reduce the risk of falling victim to phishing attacks and protect your digital identity.
Did You Hear About Our Free E-Book?
There’s much more to becoming successful in crypto, but safeguarding your digital assets is a substantial part. Best of all, it doesn’t have to be complicated. Sign up for our powerful newsletter to enhance your crypto skills right now!
Conclusion
Phishing attacks continue to evolve, becoming increasingly sophisticated. However, armed with knowledge and vigilance, you can fortify your defenses. Understanding the deception behind phishing, recognizing red flags, and adopting safe practices are your best allies in the ongoing battle for digital security. Stay informed, stay vigilant, and stay safe in the digital age!
Recommended Tools for This Article
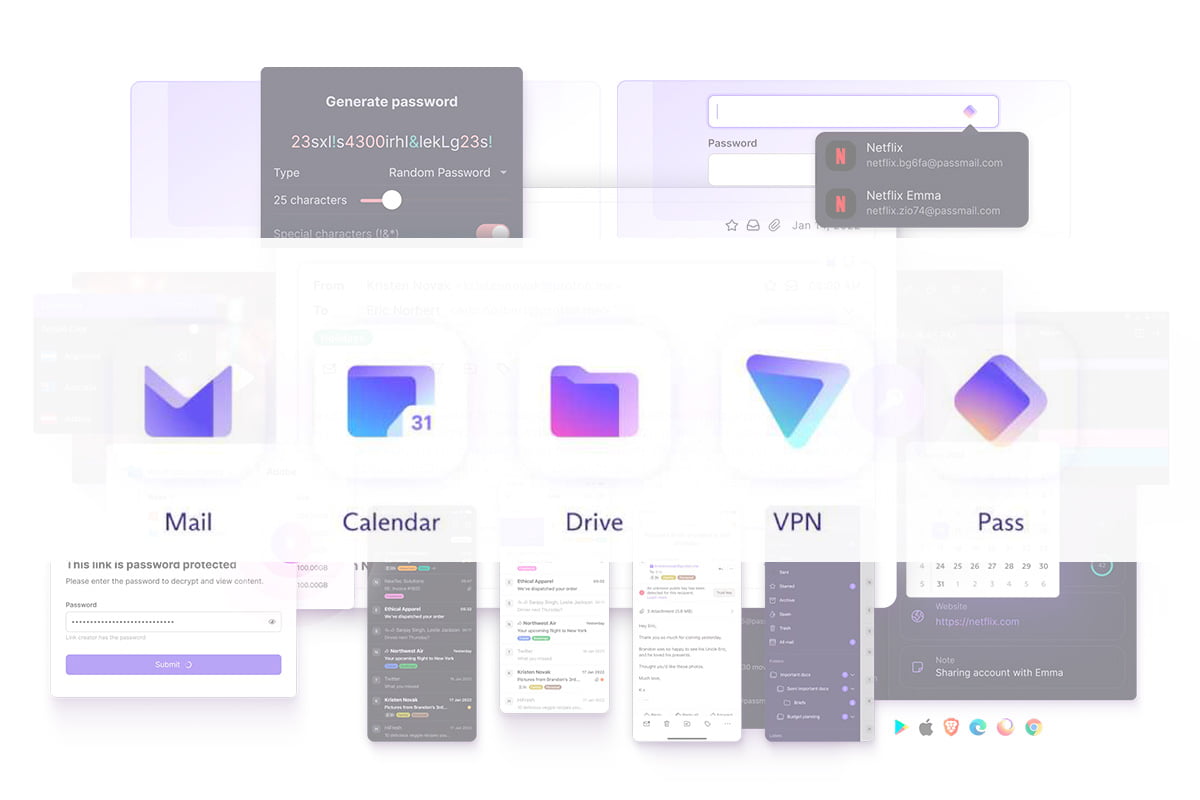
PRIVACYPROTON APPS | State-Of-The-Art Privacy Management Suite (incl. Webmail, Password Manager, Drive, VPN, and Calendar)
Proton is a Swiss-Based company that delivers the industry top-level tools to ensure your information is always yours and no one else can read it. As their slogan says "Privacy By Default" - there is much more to it. Sign-up for a free account and check by yourself.











 Don't Let Scammers Win! Discover The Ultimate Defence Strategies For Your Digital Wealth & Secure Your Crypto Future - Now!
Don't Let Scammers Win! Discover The Ultimate Defence Strategies For Your Digital Wealth & Secure Your Crypto Future - Now!