In the realm of ever-evolving cybersecurity threats, understanding what constitutes a strong password cannot be overstated. It is the first line of defense against unauthorized access to your personal and sensitive information and a crucial step for safeguarding your digital life. A strong password is a critical line of defense against unauthorized access, data breaches, and identity theft. It serves as a digital lock that keeps your online accounts safe and secure.
Password Entropy: The Key to Strength
The strength of a password is often measured in terms of entropy. Entropy is a measure of randomness and unpredictability. In the context of passwords, higher entropy means a more secure password. It’s the foundation of a strong password as it makes it extremely difficult for both computers and humans to guess. So, what contributes to password entropy?
1. Length:
Longer passwords generally have higher entropy. A longer password increases the number of possible combinations, making it more resistant to brute-force attacks.
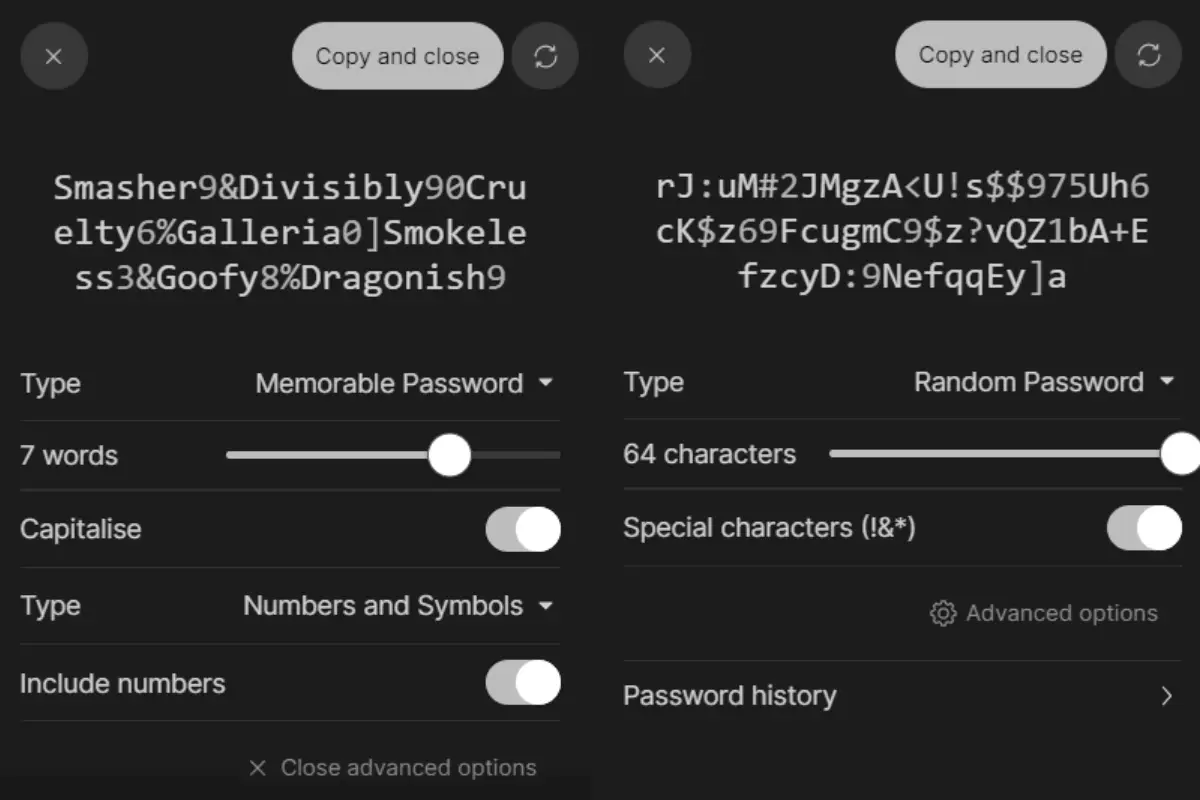
2. Complexity:
A strong password contains a mix of character types, including uppercase and lowercase letters, numbers, and special symbols. This diversity increases entropy.
3. Unpredictability:
Passwords should not follow easily guessable patterns, such as common words, phrases, or sequences. Predictable patterns lower entropy.
4. Uniqueness:
Avoid using the same password for multiple accounts. Reusing passwords can lead to vulnerabilities if one account is compromised.
5. Randomness:
Truly random combinations of characters yield high entropy. This is where humans often falter in creating strong passwords.
“Through 20 years of effort, we’ve successfully trained everyone to use passwords that are hard for humans to remember, but easy for computers to guess.”
Human Weakness in Password Creation
One of the biggest challenges in creating strong passwords is the human tendency to make predictable and easily guessable choices. People tend to use familiar words, phrases, or patterns in their passwords, which significantly reduces the password’s entropy. For example, many users mistakenly believe that simply reversing a word or capitalizing the last letter is enough to create a strong password. Unfortunately, this is not the case, as attackers can easily predict and exploit these patterns.
Let’s take a look at a couple of examples that illustrate the concept of entropy and the ease of guessing passwords:
Example 1: Weak Passwords That Seem To Be Strong
Here are some examples of weak passwords that incorporate character substitutions and symbols that resemble alphabet letters:
Pa$$w0rd123
– Original Word: Password
– Estimated bit strength of entropy: Approximately 29 bits
S3cur1ty!
– Original Word: Security
– Estimated bit strength of entropy: Approximately 32 bits
Ch@ng3m3
– Original Word: Change me
– Estimated bit strength of entropy: Approximately 29 bits
L0v3MyC@t
– Original Word: Love my cat
– Estimated bit strength of entropy: Approximately 36 bits
M0n3yM@k3r
– Original Word: Money maker
– Estimated bit strength of entropy: Approximately 41 bits
These passwords may appear complex due to character substitutions and symbols, but they are still relatively weak in terms of bit strength and can be vulnerable to brute-force attacks. It’s essential to use stronger and more unique passwords to enhance your online security.
Example 2: Strong Passwords That Seem To Be Weak
Surprisingly, here are some examples of passwords consisting of just four randomly selected English words and their bit strength:
Giraffe Jazz Apple Rainbow
– Estimated bit strength of entropy: Approximately 96 bits
Monkey Pizza Sunflower Mountain
– Estimated bit strength of entropy: Approximately 104 bits
BasketballCandlestickOceanDreamer
– Estimated bit strength of entropy: Approximately 108 bits
ElephantWhisperingStrawberrySailboat
– Estimated bit strength of entropy: Approximately 112 bits
FireworkRainforestTigerLighthouse
– Estimated bit strength of entropy: Approximately 124 bits
Using four random dictionary words in a password significantly increases its bit strength and overall security compared to passwords with character substitutions and symbols. These passphrases are stronger and more resistant to brute-force attacks. However, you cannot choose the words to your liking or even try to “pretend” that you are picking them randomly. For the password to be genuinely strong, it must be generated from real “chaos,” a task that only a computer (or rather a password manager app) can handle.
CRYPTO TOOLBOX
How Long Would It Take To Crack Your Password?
Let’s calculate the time it would take to brute force a 29-bit password with the assumption of a typical computational power, which might be in the range of millions of guesses per second.
Let’s assume the attacker’s computer can test 1 million (10^6) password guesses per second.
Number of Combinations = 2^29 ≈ 536,870,912
Password Guesses per Second = 1,000,000 (1 million)
Time = Number of Combinations / Password Guesses per Second
Time ≈ 536,870,912 / 1,000,000 ≈ 536.87 seconds
So, with a more average estimate of 1 million password guesses per second, it would take approximately 536.87 seconds to brute force a 29-bit password. This is roughly 9 minutes, which is significantly longer than the previous high-end estimate but still relatively short. Therefore, it underscores the importance of using longer and more complex passwords or passphrases for better security.
Now, if the attacker uses a more advanced computational power available the results would change drastically:
1. Computational Power: Let’s assume the attacker is using a powerful computer that can test 1 billion (10^9) password guesses per second. This is a relatively high-end estimate.
2. Bit Strength: A 29-bit password would have 2^29 possible combinations.
With these assumptions, we can calculate the time it would take to brute force the password:
Number of Combinations = 2^29 ≈ 536,870,912
Password Guesses per Second = 1,000,000,000 (1 billion)
Time = Number of Combinations / Password Guesses per Second
Time ≈ 536,870,912 / 1,000,000,000 ≈ 0.54 seconds
So, with a high-end estimate of 1 billion password guesses per second, it would take approximately 0.54 seconds to brute force a 29-bit password. However, it’s important to note that this calculation assumes the attacker is incredibly efficient and has access to a powerful computer. In practice, a strong password should have much higher bit strength to resist brute force attacks effectively.
While for the weaker passwords, it makes not much of a difference for you whether it takes 500 sec or 0.5 sec, have a look at how it changes for stronger passwords.
A very good example of how increasing the length adds to password security is demonstrated with the online tool developed by security.org
Here’s a table summarizing the time it would take to brute force passwords with different bit strengths using both typical and powerful computational power:
Password Bit Strength |
Typical Computational Power(1 million/sec) |
Advanced Computational Power(1 billion/sec) |
| 29 bits | 9 minutes | 0.54 seconds |
| 40 bits | 12.7 days | 18 minutes |
| 64 bits | 584,942 years | 585 years |
This table illustrates the significant increase in security as the password bit strength increases. A 64-bit password provides a much higher level of security compared to 29-bit and 40-bit passwords, making it much more resistant to brute-force attacks.
How Much Would It Cost To Brute-Force Your Password?
Now, an important question arises: How much would it cost to crack your password, and what is the attacker’s motivation to do so?
Keep in mind that conducting a cyber attack also generates costs for the hacker.
On average, renting cloud computing power (such as AWS) ranges from $1 to approximately $30 per hour (for the fastest data processing). As processor speeds advance over time, the price range remains similar.
If cracking your password would cost more than it would be worth, who would do that? At the very least, it’s a rule of thumb to exercise maximum discretion when it comes to valuable digital assets, so perhaps there’s no point in bragging about it.
What About The Moore’s Law?
Moore’s Law, which originally posited that the number of transistors on a microchip would double approximately every two years, has historically driven rapid advances in computational power. However, the rate of progress described by Moore’s Law has slowed in recent years, and it is uncertain how long it will continue to hold. Nevertheless, we can make some speculative calculations based on historical trends to estimate how Moore’s Law might affect the calculations for password cracking times on both typical and extremely powerful computers.
Here are some hypothetical estimates, assuming Moore’s Law continues to hold for the next few decades:
1. Typical Computational Power (1 million guesses per second):
– Password Bit Strength: 40 bits
– Estimated Time (as of 2023): 12.7 days
– Estimated Time (10 years later, 2033): Approximately 1.27 hours
2. Advanced Computational Power (1 billion guesses per second):
– Password Bit Strength: 40 bits
– Estimated Time (as of 2023): 18 minutes
– Estimated Time (10 years later, 2033): ———–
Please note that these estimates are highly speculative and simplified. Moore’s Law may not hold at the same pace for all types of computational tasks, and other factors can also influence computational power, such as advances in parallel computing, quantum computing, and algorithms designed to optimize specific tasks.
It’s highly likely that what we consider powerful computing today will indeed change significantly over the course of a decade, even without relying solely on the traditional Moore’s Law projection.
Technological advancements, shifts in hardware architecture, and breakthroughs in high-performance computing (Quantum Computers) can lead to substantial improvements in computational power over a relatively short period. As such, the estimate for “Powerful Computational Power” should be considered a rough approximation. The actual capabilities of powerful computing systems in 10 years could be substantially different and potentially much greater.
‘Does and Don’ts’ for Generating Strong Passwords
To create strong passwords, follow this advice:
Use a Password Manager
Consider using a reputable password manager.
A password manager is a powerful tool that can significantly enhance your online security. It creates and stores unique and complex passwords for each of your accounts, removing the need for you to remember them. Here’s what you need to know about password managers:
– Password managers generate strong passwords that are nearly impossible for a human to guess.
– They securely store multiple passwords and responses to security questions.
– Passwords are protected by a single master password or passphrase.
– Passwords can be synchronized across your devices, making them accessible from anywhere.
Creating Strong Passphrases with Dice
If you don’t use a Password Manager, the next (and the only option) is using dice. Creating strong and memorable passphrases is crucial for enhanced security, especially for your device passwords, full-disk encryption, and password manager master passphrase. An effective method is to use dice and a word list to randomly choose words. To maximize security, it’s recommended to select a minimum of six words for your passphrase. Longer and more random passphrases are harder for both computers and humans to guess.
Create Long Passwords
Longer passwords are stronger. Aim for at least 12 characters.
Include Variety
Use a mix of uppercase and lowercase letters, numbers, and special symbols.
Avoid Predictable Patterns
Steer clear of common words, phrases, or easily guessable patterns.
Don't Reuse Passwords
Each account should have its unique password. Reusing passwords across multiple accounts is a risky security practice. If a malicious actor gains access to one of your passwords, they can potentially compromise all of your accounts that share the same password. To mitigate this risk, it’s essential to use unique passwords for each account.
Don't Include Personal Information
Don’t use easily discoverable information like your name, birthdate, or common words associated with you.
Don't Manually Pick Dictionary Word
Avoid manually choosing complete words found in dictionaries (Use a dice, instead, or let a designated app do the job for you)
Don't Share Your Password
Never share your password with anyone, including family and friends. If you ever have to do so, use a password sharing feature found in some of the manager apps.
Don't Use Online Password Generators
While you can be tempted to simply type in and search Google for “online password generator” – there’s not many things that could threten your security more than that. You have no idea who else sees the password you just created! Instead – use a professional password manager with ZERO-KNOWLEDGE encryption!
Don't Store Your Passwords Unencrypted
Do not keep your passwords in a notepad or an Excel file on your hard drive (or in a cloud). It can be easily intercepted if your computer is compromised or online service suffers an exploit. Additionally, some cloud storage companies (such as Google) reserve full rights to access your data with no restrictions!
Why Isn’t Entropy the Sole Determinant of Password Strength?
It’s surprising how even simple modifications to passwords, such as using character substitutions, can significantly increase their entropy and, therefore, their security. However, it’s important to remember that while high entropy is a good measure of password strength, other factors, such as unpredictability, also play a role in password security.
For instance, it doesn’t matter how high the entropy of your password is if someone who knows you (or a hacker who has gathered a decent amount of information about you) can guess most of it.
As an example, you might think that if your password is: “Seeking no truth. Winning is all. Find it so grim. So true. So real.” – it would take light years to brute-force your password. Nothing more wrong. Just try Google…
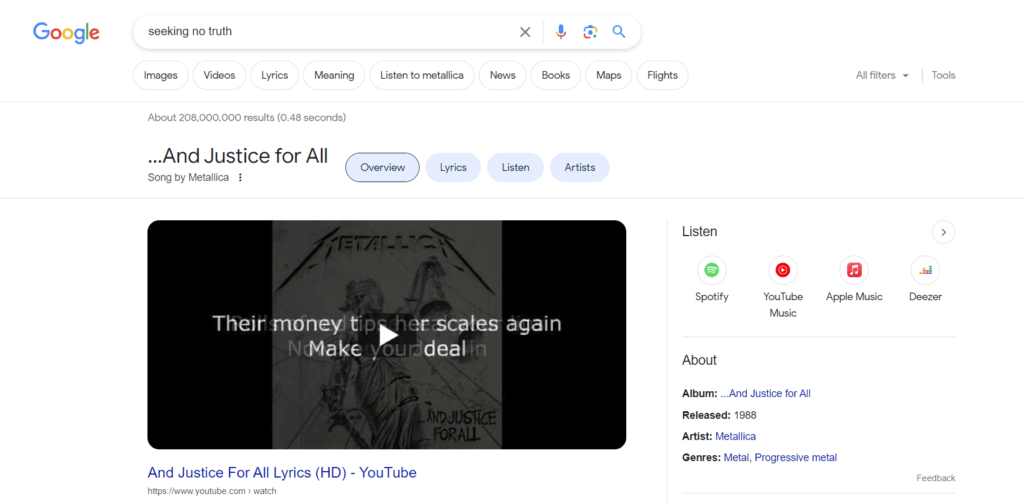
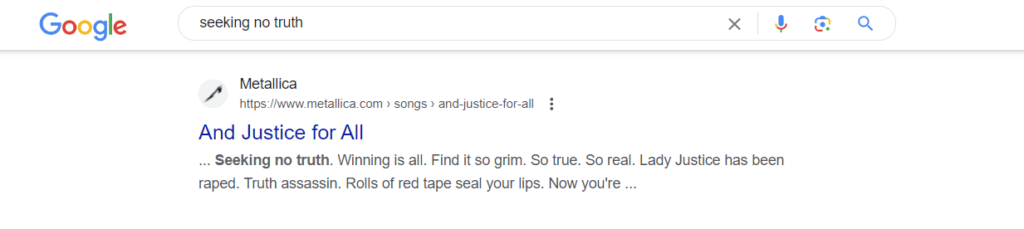
For the highest level of security, consider using passphrases, which are longer phrases or sentences. Longer passwords, when combining uppercase and lowercase letters, numbers, and special characters in a random or unpredictable manner, are even more secure.
Additionally, using a unique password for each online service and regularly updating passwords can further enhance your overall security. Password managers are helpful tools for generating and managing strong, unique passwords for all your accounts.
Additional Considerations
The Importance of Two-Factor Authentication (2FA)
Two-factor authentication adds an extra layer of security to your accounts. It requires two components for access: your password and a second factor, which can be a one-time secret code or a number generated by a mobile app or hardware device. When enabling 2FA:
– Choose an authenticator application or a stand-alone hardware device over SMS text messages for code delivery.
– Some services offer one-time passwords that are meant to be written down and carried with you. These can be more secure in case your phone is compromised.
– Consider using optional backups for your security codes, but be mindful of their security trade-offs.
Dealing with Security Questions
Be cautious when answering security questions on websites. Honest answers to these questions are often publicly discoverable facts, which can be exploited by determined adversaries. Instead, provide fictional answers that only you know, or generate random answers using your password manager. Avoid using the same answers for multiple accounts on different websites or services.
Did You Know That You Can Learn A Safe Way To Generate Passive Yield With Your Crypto Over The Next Decade?
Unlock the power of digital assets with HEX Passive Income. This course takes you from novice to pro in the world of cryptocurrency investments in just a few weeks. Learn the secrets of yield farming, PulseChain staking, and the HEX staking ladder system. Get started today for financial freedom.
Did You Hear About Our Free E-Book?
There’s much more to becoming successful in crypto, but safeguarding your digital assets is a substantial part. Best of all, it doesn’t have to be complicated. Sign up for our powerful newsletter to enhance your crypto skills right now!
Conclusion
By understanding what makes a strong password and following these guidelines, you can significantly enhance your online security and protect your valuable digital assets from potential threats and breaches. Remember that strong passwords are a fundamental component of a robust cybersecurity strategy. When creating your passwords, prioritize both security and ease of memory, if possible.
Recommended Tools for This Article
PRIVACYPROTON APPS | State-Of-The-Art Privacy Management Suite (incl. Webmail, Password Manager, Drive, VPN, and Calendar)
Proton is a Swiss-Based company that delivers the industry top-level tools to ensure your information is always yours and no one else can read it. As their slogan says “Privacy By Default” – there is much more to it. Sign-up for a free account and check by yourself.











 Don't Let Scammers Win! Discover The Ultimate Defence Strategies For Your Digital Wealth & Secure Your Crypto Future - Now!
Don't Let Scammers Win! Discover The Ultimate Defence Strategies For Your Digital Wealth & Secure Your Crypto Future - Now!